Securing cellular connectivity has never been more crucial in our increasingly connected world. According to IBM, the average cost of a data breach surged by 15% over three years, reaching $4.45 million in 2023. This substantial rise in expenses is a key driver behind the growing investment in security measures across organizations. (source: https://www.ibm.com/reports/data-breach)
One notable example of connectivity vulnerabilities occurred when a remote hack of a Jeep Cherokee‘s cellular system led Fiat Chrysler to recall 1.4 million vehicles. The issue stemmed from the cellular provider’s allowance of SIM-to-SIM traffic. In another case, security weaknesses in 3G and 4G modems from manufacturers like Sierra and Huawei left cellular-connected IoT devices exposed to potential remote attacks.
In 2016, the Mirai botnet exploited weaknesses in connected devices, causing widespread disruptions to major online services like Twitter and Netflix. The root cause was identified as cellular providers’ failure to block inbound traffic. So, how can organizations enhance corporate security without shelling out millions?
1. Device Authentication: Ensuring Device Integrity
Securing IoT devices starts with robust device authentication. Network-driven IMEI management plays a crucial role here, ensuring that SIM cards are only operational within their designated devices—be it a laptop, tablet, phone, or other IoT equipment. This not only prevents unauthorized use but also alerts organizations to any attempts to misuse the SIM card.
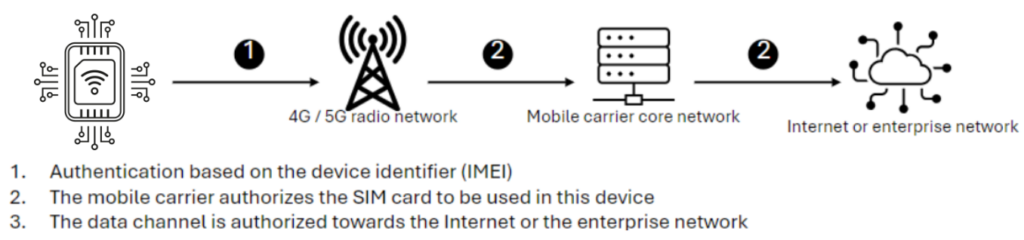
The SIM Secure Vault provides features like encrypted messaging directly to the SIM and the ability to store sensitive data securely. This functionality allows the SIM to receive encrypted credentials and act as a secure element for application authentication.
2. Unbreakable Data Security: From Edge to Server
Traditional VPNs often fall short when it comes to data security for Cellular Enabled IoT Devices.
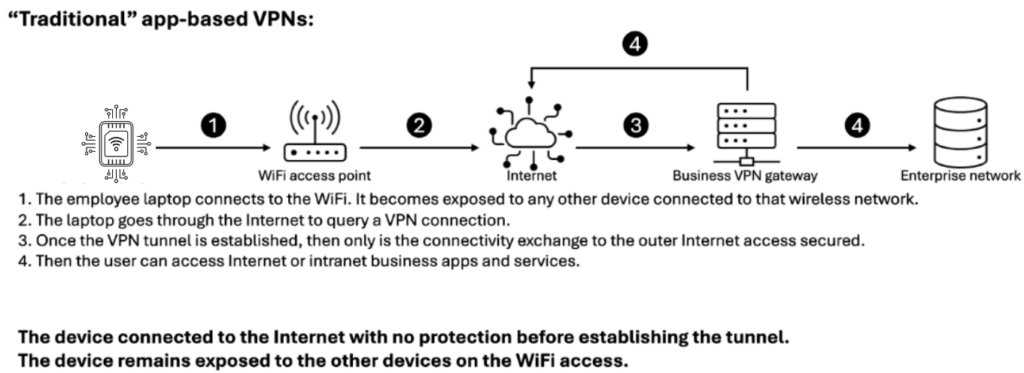
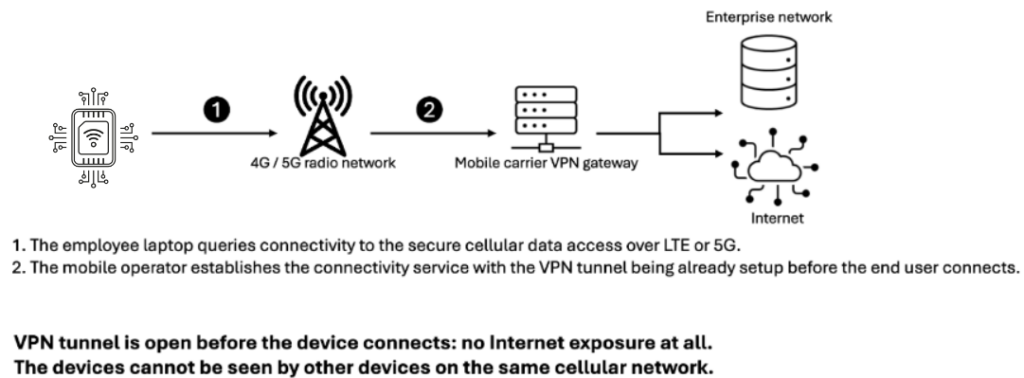
Carrier-grade VPNs over cellular networks offer a robust alternative. By routing data traffic directly from the IoT device to the mobile operator’s core network and then to the enterprise network through optimized pathways, these solutions bypass the inefficiencies of the public Internet.
This approach delivers:
- End-to-end encryption with Zero Trust principles
- Minimal exposure to the public internet
- Enhanced performance with improved bandwidth and latency
3. Post-Control: 24/7 Oversight of Your Connected World
Once your devices are operational, continuous monitoring becomes crucial. Advanced behavior and usage management tools enable you to set expectations for device performance. For example, if a device consumes excessive data within a specified period, the platform can alert your systems and even automatically suspend its SIM card. Comprehensive behavior reports ease the tracking of devices and prompt resolution of any anomalies.
How does Transatel Lead the Way?
Transatel’s Global Cellular Connectivity solution provides seamless IoT connectivity over 4G-LTE and 5G in over 200 territories. Our unique global core network offers a significant advantage: unlike traditional systems that funnel data to a central point, our setup ensures maximum performance regardless of the device’s location. In today’s world, where secure and reliable connectivity is crucial, our solution delivers carrier-grade VPNs over cellular data, making it the premier choice for enterprise security.
By leveraging our cellular connectivity, businesses can benefit from robust security mechanisms and efficient data management solutions. This approach helps ensure that cellular-enabled IoT devices run within a secure network, reducing risks, boosting productivity, and minimizing cybersecurity vulnerabilities.
Ask our experts here to learn more about secure IoT cellular connectivity and solutions by Transatel.